Software-update: Mozilla Thunderbird 128.1.1 - Computer - Downloads - Tweakers
Software-update: Mozilla Firefox 129.0.2 - Computer - Downloads - Tweakers
Mozilla onderzoekt waarom Dell in Engeland geld vraagt voor Firefox-installatie - Computer - Nieuws - Tweakers
Software-update: Mozilla Firefox 129.0.1 - Computer - Downloads - Tweakers
Software-update: Mozilla Thunderbird 115.14.0 - Computer - Downloads - Tweakers
Here’s what we’re working on in Firefox
We recently shared a number of updates with our community of users, and now we want to share them here:
At Mozilla, we work hard to make Firefox the best browser for you. That’s why we’re always focused on building a browser that empowers you to choose your own path, that gives you the freedom to explore without worry or compromises. We’re excited to share more about the updates and improvements we have in store for you over the next year.
Bringing you the features you’ve been asking forWe’ve been listening to your feedback, and we’re prioritizing the features you want most.
- Productivity boosters like
- Tab Grouping, Vertical Tabs, and our handy Sidebar will help you stay organized no matter how many tabs you have open — whether it’s 7 or 7,500.
- Plus, our new Profile Management system will help keep your school, work, and personal browsing separate but easily accessible.
- Customizable new tab wallpapers that will let you choose from a diverse range of photography, colors, and abstract images that suits you most.
- Intuitive privacy settings that deliver all the power of our world-class anti-tracking technologies in a simplified, easy-to-understand way.
- More streamlined menus that reduce visual clutter and prioritize top user actions so you can get to the important things quicker.
Speed is everything when you’re online, so we’re continuing to work hard to make Firefox as fast and efficient as possible. You can expect even faster, smoother browsing on Firefox, thanks to quicker page loads and startup times – all while saving more of your phone’s battery life. We’ve already improved responsiveness by 20 percent as measured by Speedometer 3, a collaboration we’ve spearheaded with other leading tech companies. And in that collaborative spirit, we’re also working with the Interop project to make it easy for people to build sites that work great across all browsers. We value your support in our efforts to improve cross-browser compatibility which is why we’ve added new features to easily report when websites aren’t working quite right; this feedback is critical as we look to address even small functionality issues that affect your day-to-day online experience.
Making the most of your time online — without sacrificeEnsuring your privacy is core to everything we do at Firefox. Unlike other companies, who ask you to exchange your data in order to do even basic, everyday things online — you don’t have to give up your personal information to get a faster, more efficient browser experience with Firefox. Reading a news story in a different language or signing a form for school or work shouldn’t require you to give up your privacy. So, we’ve worked hard to make things like translation and PDF editing in Firefox happen locally on your device, so you don’t have to ship off your personal data to a server farm for a company to use it how they see fit — to keep tabs on you, sell your information to the highest bidder, or train their AI. With Firefox, you have a lot of choice — but you don’t have to choose between utility and privacy. Your data is secure, and most importantly, just yours.
We are approaching the use of AI in Firefox — which many, many of you have been asking about — in the same way. We’re focused on giving you AI features that solve tangible problems, respect your privacy, and give you real choice.
We’re looking at how we can use local, on-device AI models — i.e., more private — to enhance your browsing experience further. One feature we’re starting with next quarter is AI-generated alt-text for images inserted into PDFs, which makes it more accessible to visually impaired users and people with learning disabilities.
Join us on this journeyOur progress is driven by a vibrant community of users and developers like you. We encourage you to contribute to our open-source projects and to engage with us on Mozilla Connect or Discourse, and check out our recent AMA on Reddit. Your participation is crucial in shaping what Firefox becomes next.
The post Here’s what we’re working on in Firefox appeared first on The Mozilla Blog.
Wladimir Palant: How insecure is Avast Secure Browser?
A while ago I already looked into Avast Secure Browser. Back then it didn’t end well for Avast: I found critical vulnerabilities allowing arbitrary websites to infect user’s computer. Worse yet: much of it was due to neglect of secure coding practices, existing security mechanisms were disabled for no good reason. I didn’t finish that investigation because I discovered that the browser was essentially spyware, collecting your browsing history and selling it via Avast’s Jumpshot subsidiary.
But that was almost five years ago. After an initial phase of denial, Avast decided to apologize and to wind down Jumpshot. It was certainly a mere coincidence that Avast was subsequently sold to NortonLifeLock, called Gen Digital today. Yes, Avast is truly reformed and paying for their crimes in Europe and the US. According to the European decision, Avast is still arguing despite better knowledge that their data collection was fully anonymized and completely privacy-conformant but… well, old habits are hard to get rid of.
Either way, it’s time to take a look at Avast Secure Browser again. Because… all right, because of the name. That was a truly ingenious idea to name their browser like that, nerd sniping security professionals into giving them free security audits. By now they certainly would have addressed the issues raised in my original article and made everything much more secure, right?

Note: This article does not present any actual security vulnerabilities. Instead, this is a high-level overview of design decisions that put users at risk, artificially inflating the attack surface and putting lots of trust into the many, many companies involved with the Avast webspaces. TL;DR: I wouldn’t run Avast Secure Browser on any real operating system, only inside a virtual machine containing no data whatsoever.
Contents- Summary of the findings
- What is Avast Secure Browser?
- The pre-installed extensions
- Super-powered websites
The issues raised in my original article about the pre-installed browser extensions are still partially present. Two extensions are relaxing the default protection provided by Content-Security-Policy even though it could have been easily avoided. One extension is requesting massive privileges, even though it doesn’t actually need them. At least they switched from jQuery to React, but they still somehow managed to end up with HTML injection vulnerabilities.
In addition, two extensions will accept messages from any Avast website – or servers pretending to be Avast websites, since HTTPS-encrypted connections aren’t being enforced. In the case of the Privacy Guard (sic!) extension, this messaging exposes users’ entire browsing information to websites willing to listen. Yes, Avast used to collect and sell that information in the past, and this issue could in principle allow them to do it again, this time in a less detectable way.
The Messaging extension is responsible for the rather invasive “onboarding” functionality of the browser, allowing an Avast web server to determine almost arbitrary rules to nag the user – or to redirect visited websites. Worse yet, access to internal browser APIs has been exposed to a number of Avast domains. Even if Avast (and all the other numerous companies involved in running these domains) are to be trusted, there is little reason to believe that such a huge attack surface can possibly be secure. So it has to be expected that other websites will also be able to abuse access to these APIs.
What is Avast Secure Browser?Avast Secure Browser is something you get automatically if you don’t take care while installing your Avast antivirus product. Or AVG antivirus. Or Avira. Or Norton. Or CCleaner. All these brands belong to Gen Digital now, and all of them will push Avast Secure Browser under different names.
According to their web page, there are good reasons to promote this browser:

So one of the reasons is: this browser is 100% free. And it really is, as in: “you are the product.” I took the liberty of making a screenshot of the browser and marking the advertising space:

Yes, maybe this isn’t entirely fair. I’m still indecisive as to whether the search bar should also be marked. The default search engine is Bing and the browser will nudge you towards keeping it selected. Not because Microsoft’s search engine is so secure and private of course but because they are paying for it.
But these are quality ads and actually useful! Like that ad for a shop selling food supplements, so that you can lead a healthy life. A quick search reveals that one of the three food supplements shown in the ad is likely useless with the suspicion of being harmful. Another brings up lots of articles by interested parties claiming great scientifically proven benefits but no actual scientific research on the topic. Finally the third one could probably help a lot – if there were any way of getting it into your body in sufficient concentration, which seems completely impossible with oral intake.
Now that we got “free” covered, we can focus on the security and privacy aspects in the subsequent sections.
The pre-installed extensionsThere are various reasons for browser vendors to pre-package extensions with their browser. Mozilla Firefox uses extensions to distribute experimental features before they become an integral part of the browser. As I learned back in 2011, Google Chrome uses such extensions to promote their web applications and give them an advantage over competition. And as Simon Willison discovered only a few days ago, the Google Hangouts extension built into Google Chrome gives Google domains access to internal browser APIs – quite nifty if one wants better user tracking capabilities.
My previous article mentioned Avast Secure Browser adding eleven extensions to the ones already built into Google Chrome. This number hasn’t changed: I still count eleven extensions, even though their purposes might have changed. At least that’s eleven extensions for me, differently branded versions of this browser seem to have a different combination of extensions. Only two of these extensions (Coupons and Video Downloader) are normally visible in the list of extensions and can be easily disabled. Three more extensions (Avast Bank Mode, Avast SecureLine VPN, Privacy Guard) become visible when Developer Mode is switched on.

And then there are five extensions that aren’t visible at all and cannot be disabled by regular means: Anti-Fingerprinting, Messaging, Side Panel, AI Chat, Phishing Protection. Finally, at least the New Tab extension is hardwired into the browser and is impossible to disable.
Now none of this is a concern if these extensions are designed carefully with security and privacy in mind. Are they?
Security mechanisms disabledMy previous article described the Video Downloader extension as a huge “please hack me” sign. Its extension manifest requested every permission possible, and it also weakened Content-Security-Policy (CSP) protection by allowing execution of dynamic scripts. Both were completely unnecessary, my proof of concept exploit abused it to get a foothold in the Avast Secure Browser.
Looking at the current Video Downloader manifest, things are somewhat better today:
{ "content_security_policy": "script-src 'self' 'unsafe-eval'; object-src 'self'", "permissions": [ "activeTab", "downloads", "management", "storage", "tabs", "webRequest", "webRequestBlocking", "<all_urls>" ], }The permissions requested by this extension still grant it almost arbitrary access to all websites. But at least the only unused privilege on this list is management which gives it the ability to disable or uninstall other extensions.
As to CSP, there is still 'unsafe-eval' which allowed this extension to be compromised last time. But now it’s there for a reason: Video Downloader “needs” to run some JavaScript code it receives from YouTube in order to extract some video metadata.
I did not test what this code is or what it does, but this grants at the very least the YouTube website the ability to compromise this extension and, via it, the integrity of the entire browser. But that’s YouTube, it won’t possibly turn evil, right?
For reference: it is not necessary to use 'unsafe-eval' to run some untrusted code. It’s always possible to create an <iframe> element and use the sandbox attribute to execute JavaScript code in it without affecting the rest of the extension.
But there are more extensions. There is the Avast Bank Mode extension for example, and its extension manifest says:
{ "content_security_policy": "script-src 'self' 'unsafe-eval'; object-src 'self'", "permissions": [ "activeTab", "alarms", "bookmarks", "browsingData", "clipboardRead", "clipboardWrite", "contentSettings", "contextMenus", "cookies", "debugger", "declarativeContent", "downloads", "fontSettings", "geolocation", "history", "identity", "idle", "management", "nativeMessaging", "notifications", "pageCapture", "power", "privacy", "proxy", "sessions", "storage", "system.cpu", "system.display", "system.memory", "system.storage", "tabCapture", "tabs", "tts", "ttsEngine", "unlimitedStorage", "webNavigation", "webRequest", "webRequestBlocking", "http://*/*", "https://*/*", "<all_urls>" ], }Yes, requesting every possible permission and allowing execution of dynamic scripts at the same time, the exact combination that wreaked havoc last time. Why this needs 'unsafe-eval'? Because it uses some ancient webpack version that relies on calling eval() in order to “load” JavaScript modules dynamically. Clearly, relaxing security mechanisms was easier than using a better module bundler (like the one used by other Avast extensions).
The (lack of) ad blocking privacyThe Privacy Guard extension is responsible for blocking ads and trackers. It is meant by the sentence “block ads and boost your online privacy” in the website screenshot above. It is also one of the two extensions containing the following entry in its manifest:
{ "externally_connectable": { "ids": [ "*" ], "matches": [ "*://*.avastbrowser.com/*", "*://*.avgbrowser.com/*", "*://*.ccleanerbrowser.com/*", "*://*.avast.com/*", "*://*.securebrowser.com/*" ] }, }What this means: any other extension installed is allowed to send messages to the Privacy Guard extension. That isn’t restricted to Avast extensions, any other extension you installed from Avast’s or Google’s add-on store is allowed to do this as well.
The same is true for any website under the domains avast.com, securebrowser.com, avastbrowser.com, avgbrowser.com or ccleanerbrowser.com. Note that the rules here don’t enforce https:// scheme, unencrypted HTTP connections will be allowed as well. And while avast.com domain seems to be protected by HTTP Strict Transport Security, the other domains are not.
Why this matters: when your browser requests example.securebrowser.com website over an unencrypted HTTP connection, it cannot be guaranteed that your browser is actually talking to an Avast web server. In fact, any response is guaranteed to come from a malicious web server because to such website exists.
One way you might get a response from such a malicious web server is connecting to a public WiFi. In principle, anyone connected to the same WiFi could redirect unencrypted web requests to their own malicious web server, inject an invisible request to example.securebrowser.com in a frame (which would also be handled by their malicious server) and gain the ability to message Privacy Guard extension. While not common, this kind of attack did happen in the wild.
And what does someone get then? Let me show you:
chrome.runtime.connect("onochehmbbbmkaffnheflmfpfjgppblm", {name: "PG_STORE"}) .onMessage.addListener(x => console.log(x));This establishes a connection to the extension and logs all incoming messages. One message is received immediately:
{ "type": "chromex.state", "payload": { "main": { "settings": { "paused": false, "off": false, "blockingMode": "strict", "showIconBadge": true, "fingerprintEnabled": true, "previousBlockingModeIsOff": false }, "pausedDomains": [], "whitelist": [], "afpWhitelist": [], "installationInfo": { "hostPrefix": "", "noProBrand": false, "urls": { "faqUrl": "https://extension.securebrowser.com/privacy-guard/learn-more/", "proUrl": "https://extension.securebrowser.com/privacy-guard/offer/" }, "whitelists": { "whitelist": "https://update.avastbrowser.com/adblock/assets/v3/document_whitelist.txt", "filterWhitelist": "https://update.avastbrowser.com/adblock/assets/v3/filter_whitelist.txt", "searchWhitelist": "https://update.avastbrowser.com/adblock/assets/v3/search_document_whitelist.txt" } }, "isProUser": false, "blockedAdsCount": 12 }, "tabs": { "391731034": { "adsBlocked": 0, "fingerprintAttempts": 0, "adsAllowed": 0, "listAdsBlocked": [], "listAdsAllowed": [], "pageAllowed": false, "isInternal": false, "domainIsPaused": false, "isInUserWhitelist": false, "isInUserAfpWhitelist": false, "netFilteringSwitch": true, "active": true, "audible": false, "autoDiscardable": true, "discarded": false, "groupId": -1, "height": 514, "highlighted": true, "id": 391731034, "incognito": false, "index": 2, "lastAccessed": 1720641256405.484, "mutedInfo": { "muted": false }, "openerTabId": 391731032, "pendingUrl": "secure://newtab/", "pinned": false, "selected": true, "status": "complete", "title": "Example Domain", "url": "https://example.com/", "width": 299, "windowId": 391730998, "favIconUrl": "https://example.com/favicon.ico" }, "-1": { "adsBlocked": 0, "fingerprintAttempts": 0, "adsAllowed": 0, "listAdsBlocked": [], "listAdsAllowed": [], "isInternal": true }, "active": 391731034 } } }The first part are the Privacy Guard settings, your whitelisted domains, everything. There are also the three hardcoded lists containing blocking exceptions – funny how Avast doesn’t seem to mention these anywhere in the user interface or documentation. I mean, it looks like in the default “Balanced Mode” their ad blocker won’t block any ads on Amazon or eBay among other things. Maybe Avast should be more transparent about that, or people might get the impression that this has something to do with those sponsored bookmarks.
And then there is information about all your browsing tabs which I shortened to only one tab here. It’s pretty much all information produced by the tabs API, enriched with some information on blocked ads. Privacy Guard will not merely send out the current state of your browsing session, it will also send out updates whenever something changes. To any browser extension, to any Avast website and to any web server posing as an Avast website.
Does Avast abuse this access to collect users’ browsing data again? It’s certainly possible. As long as they only do it for a selected subset of users, this would be very hard to detect however. It doesn’t help that Avast Secure Browser tracks virtual machine usage among other things, so it’s perfectly plausible that this kind of behavior won’t be enabled for people running one. It may also only be enabled for people who opened the browser a given number of times after installing it, since this is being tracked as well.
Can other browser extensions abuse this to collect users’ browsing data? Absolutely. An extension can declare minimal privileges, yet it will still be able to collect the entire browsing history thanks to Privacy Guard.
Can a malicious web server abuse this to collect users’ browsing data beyond a single snapshot of currently open tabs? That’s more complicated since this malicious web server would need its web page to stay open permanently somehow. While Avast has the capabilities to do that (more on that below), an arbitrary web server normally doesn’t and has to resort to social engineering.
The messaging interface doesn’t merely allow reading data, the data can also be modified almost arbitrarily as well. For example, it’s possible to enable ad blocking without any user interaction. Not that it changes much, the data collection is running whether ad blocking is enabled or not.
This messaging interface can also be used to add exceptions for arbitrary domains. And while Privacy Guard options page is built using React.js which is normally safe against HTML injections, in one component they chose to use a feature with the apt name dangerouslySetInnerHTML. And that component is used among other things for displaying, you guessed it: domain exceptions.
This is not a Cross-Site Scripting vulnerability, thanks to CSP protection not being relaxed here. But it allows injecting HTML content, for example CSS code to mess with Privacy Guard’s options page. This way an attacker could ensure that exceptions added cannot be removed any more. Or they could just make Privacy Guard options unusable altogether.
The onboarding experienceThe other extension that can be messaged by any extension or Avast web server is called Messaging. Interestingly, Avast went as far as disabling Developer Tools for it, making it much harder to inspect its functionality. I don’t know why they did it, maybe they were afraid people would freak out when they saw the output it produces while they are browsing?

You wonder what is going on? This extension processes some rules that it downloaded from https://config.avast.securebrowser.com/engagement?content_type=messaging,messaging_prefs&browser_version=126.0.25496.127 (with some more tracking parameters added). Yes, there is a lot of info here, so let me pick out one entry and explain it:
{ "post_id": 108341, "post_title": "[190] Switch to Bing provider – PROD; google", "engagement_trigger_all": [ { "parameters": [ { "operator": "s_regex", "value": "^secure:\\/\\/newtab", "parameter": { "post_id": 11974, "name": "url_in_tab", "post_title": "url_in_tab", "type": "string" } } ] }, { "parameters": [ { "operator": "s_regex", "value": "google\\.com", "parameter": { "post_id": 25654, "name": "setting_search_default", "post_title": "setting_search_default (search provider)", "type": "string" } } ] } ], "engagement_trigger_any": [ { "parameters": [ { "operator": "equals", "value": "0", "parameter": { "post_id": 19236, "name": "internal.triggerCount", "post_title": "internal.triggerCount", "type": "number" } } ] }, { "parameters": [ { "operator": "n_gte", "value": "2592000", "parameter": { "post_id": 31317, "name": "functions.interval.internal.triggered_timestamp", "post_title": "interval.internal.triggered_timestamp", "type": "number" } } ] } ], "engagement_trigger_none": [], … }The engagement_trigger_all entry lists conditions that have all be true: you have to be on the New Tab page, and your search provider has to be Google. The engagement_trigger_any entry lists conditions where any one is sufficient: this particular rule should not have been triggered before, or it should have been triggered more than 2592000 seconds (30 days) ago. Finally, engagement_trigger_none lists conditions that should prevent this rule from applying. And if these conditions are met, the Messaging extension will inject a frame into the current tab to nag you about switching from Google to Bing:

Another rule will nag you every 30 days about enabling the Coupons extension, also a cash cow for Avast. There will be a nag to buy the PRO version for users opening a Private Browsing window. And there is more, depending on the parameters sent when downloading these rules probably much more.
An interesting aspect here is that these rules don’t need to limit themselves to information provided to them. They can also call any function of private Avast APIs under the chrome.avast, chrome.avast.licensing and chrome.avast.onboarding namespaces. Some API functions which seem to be called in this way are pretty basic like isPrivateWindow() or isConnectedToUnsafeWifi(), while gatherInfo() for example will produce a whole lot of information on bookmarks, other browsers and Windows shortcuts.
Also, displaying the message in a frame is only one possible “placement” here. The Messaging extension currently provides eight different user interface choices, including straight out redirecting the current page to an address provided in the rule. But don’t worry: Avast is unlikely to start redirecting your Google searches to Bing, this would raise too many suspicions.
Super-powered websitesWhy is the Messaging extension allowing some Avast server to run browser APIs merely a side-note in my article? Thing is: this extension doesn’t really give this server anything that it couldn’t do all by itself. When it comes to Avast Secure Browser, Avast websites have massive privileges out of the box.
The browser grants these privileges to any web page under the avast.com, avg.com, avastbrowser.com, avgbrowser.com, ccleanerbrowser.com and securebrowser.com domains. At least here HTTPS connections are enforced, so that posing as an Avast website won’t be possible. But these websites automatically get access to:
- chrome.bookmarks API: full read/write access to bookmarks
- chrome.management API: complete access to extensions except for the ability to install them
- chrome.webstorePrivate API: a private browser API that allows installing extensions.
- A selection of private Avast APIs:
- chrome.avast
- chrome.avast.licensing
- chrome.avast.ntp
- chrome.avast.onboarding
- chrome.avast.ribbon
- chrome.avast.safebrowsing
- chrome.avast.safesearch
- chrome.avast.stats
- chrome.avast.themes
Now figuring out what all these private Avast APIs do in detail, what their abuse potential is and whether any of their crashes are exploitable requires more time than I had to spend on this project. I can see that chrome.avast.ntp API allows manipulating the tiles displayed on the new tab page in arbitrary ways, including reverting all your changes so that you only see those sponsored links. chrome.avast.onboarding API seems to allow manipulating the “engagement” data mentioned above, so that arbitrary content will be injected into tabs matching any given criteria. Various UI elements can be triggered at will. I’ll leave figuring out what else these can do to the readers. If you do this, please let me know whether chrome.avast.browserCall() can merely be used to communicate with Avast’s Security & Privacy Center or exposes Chromium’s internal messaging.
But wait, this is Avast we are talking about! We all know that Avast is trustworthy. After all, they promised to the Federal Trade Commission that they won’t do anything bad any more. And as I said above, impersonating an Avast server won’t be possible thanks to HTTPS being enforced. Case closed, no issue here?
Not quite, there are far more parties involved here. Looking only at www.avast.com, there is for example OneTrust who are responsible for the cookie banners. Google, Adobe, hotjar, qualtrics and mpulse are doing analytics (a.k.a. user tracking). A Trustpilot widget is also present. There is some number of web hosting providers involved (definitely Amazon, likely others as well) and at least two content delivery networks (Akamai and Cloudflare).
And that’s only one host. Looking further, there is a number of different websites hosted under these domains. Some are used in production, others are experiments, yet more appear to be abandoned in various states of brokenness. Some of these web services seem to be run by Avast while others are clearly run by third parties. There is for some reason a broken web shop run by a German e-commerce company, same that used to power Avira’s web shop before Gen Digital bought them.
If one were to count it all together, I would expect that a high two digit number of companies can put content on the domains mentioned above. I wouldn’t be surprised however if that number even went into three digits. Every single one of these companies can potentially abuse internal APIs of the Avast Secure Browser, either because they decide to make some quick buck, are coerced into cooperation by their government or their networks simply get compromised.
And not just that. It isn’t necessary to permanently compromise one of these web services. A simple and very common Cross-Site Scripting vulnerability in any one of these web services would grant any website on the internet access to these APIs. Did Avast verify the security and integrity of each third-party service they decided to put under these domains? I very much doubt so.
It would appear that the official reason for providing these privileges to so many websites was aiding the onboarding experience mentioned above. Now one might wonder whether such a flexible and extensive onboarding process is really necessary. But regardless of that, the reasonable way of doing this is limiting the attack surface. If you need to grant privileges to web pages, you grant them to a single host name. You make sure that this single host name doesn’t run any more web services than it absolutely needs, and that these web services get a proper security review. And you add as many protection layers as possible, e.g. the Content-Security-Policy mechanism which is severely underused on Avast websites.
I’ll conclude by quoting the decision to penalize Avast for their GDPR violations:
At this point, the Appellate Authority considers it necessary to recall that the Charged Company provides software designed to protect the privacy of its users. As a professional in the information and cyber field, the Charged Company is thereby also expected to be extremely knowledgeable in the field of data protection.
Yeah, well…
Don Marti: turn off advertising measurement in Apple Safari
Apple Safari includes an advertising measurement feature, but fortunately you can turn it off. I don’t regularly use this browser but can get a hold of a copy to check it, so I’ll update this if the instructions change.
On Apple iOSOpen Settings, select Safari, then scroll down to Advanced.
Turn off Privacy Preserving Ad Measurement
While you have Settings open, you might as well check two other iOS tracking features.
In Settings, go to Privacy & Security, then Tracking, and make sure “Allow Apps to Request to Track” is turned off.
Also in Settings under Privacy & Security, find “Apple Advertising” and make sure that “Personalized Ads” is turned off. (You will probably have to scroll down—Apple makes this one a little trickier to find.)
From the Safari menu, choose Settings, then check the Privacy and Advanced tabs. (On Safari - Version 16.0 (17614.1.25.9.10, 17614) it is under Privacy. On other versions you need to look under Advanced.
 <figcaption>On some versions, the setting you need is under Privacy.</figcaption>
<figcaption>On some versions, the setting you need is under Privacy.</figcaption> Uncheck Allow privacy-preserving measurement of ad effectiveness.
You can also turn off Prevent cross-site tracking if it doesn’t break any sites you use. (Some corporate web applications may still need to be updated.)
why turn this off?The deeper they hide stuff like this, the more it shows they understand that it’s not in your best interest to have it on. The Apple billboards are all about protecting you from tracking. I haven’t seen one yet that was more like Connect and share with brands you love! (please me know if you see any Apple billboards like this)
Information has value in a market. When your browser passes information about you—even in a form that is supposed to prevent individual tracking—you’re rewarding risky and problematic advertising practices along with the legit ones. Some advertising has value, but putting legit sites and malvertising on an equal basis for data collection is not helping.
Relatedturn off advertising features in Firefox
Google Chrome ad features checklist
effective privacy tips You could do privacy tips all day—this is a short list based on what has the most effect on the surveillance business.
Bonus linksNew Senate bill seeks to protect artists’ and journalists’ content from AI use (ever notice how the same Internet Thought Leaders who are surprised that people don’t want ad tracking are also surprised that people don’t want their content taken for AI?)
With a Little Help, Western Bluebirds Are Nesting in Alameda Remember, we humans cut down dead trees for safety, but that is bad for birds that are cavity nesters. Would you like to do something to improve nesting habitat? Consider installing nest boxes around your home, school, or community center.
Don Marti: PET projects or real privacy?
(update 25 Jul 2024: add links to FTC surveillance pricing story)
Every advertising event is full of thought leader insights about privacy-enhancing technologies (PETs) for ad personalization and reporting systems. Somehow Big Tech, adtech, and martech are all fired up about projects for reimplementing personalized/surveillance advertising, but this time with a bunch of complicated math added in a way that makes it hard to identify or track an individual.
In the real world, though, individualized tracking is not the top advertising privacy problem, and it might not even be in the top five. Arielle Garcia, director of intelligence for Check My Ads, said, Privacy-enhancing tech doesn’t make creepy and disruptive ads less creepy or disruptive in the eyes of the average user. And the user research backs that up. Jereth et al. find that perceived privacy violations for a browser-based system that does not target people individually are similar to the perceived violations for conventional third-party cookies. Co-author Klaus M. Miller presented the research at FTC PrivacyCon (PDF):
So keeping your data safer on your device seems to help in terms of consumer perceptions, but it doesn’t make any difference whether the firm is targeting the consumer at the individual or group level in the perceived privacy perceptions.
This might not make sense if you compare just the information passed through PETs to what is possible to do with a third-party cookie. It’s fewer total bits of information, so the users should be getting more privacy and like it better, right? Not so fast. The real problems that people complain about when they raise privacy concerns are more about information asymmetry.
People tend not to want to participate in markets in ways that give their counterparties too much information. Imagine going on vacation and visiting an old-fashioned rug market—and showing every rug merchant your budget, shopping list, and departure date. Information imbalances are not how sustainable markets work. And that’s just legit markets. The situation is even worse on today’s scam culture Internet, where the old fake it til you make it has been replaced with make it, then fake it even harder. The pervasive risks of scam culture are mostly group-level personalization risks and not the consequences of being individually identified.
Algorithmic discrimination in housing and employment ads (browser topics tracking and the prejudiced landlord problem)
Matching scammers to victims. Rob Leathern explains this problem best, in The One Simple Trick to Measuring Abuse in Tech’s $440 Billion Ads Business. When ads are personalized to the user, it’s much harder for regulators, the media, and other enforcers of laws and norms to see who’s getting what.
Personalized pricing. The FTC is investigating how companies are using AI to base pricing on consumer behavior. You can be sorted into a low-price or high-price bucket without being individually tracked. More from Cory Doctorow: FTC vs surveillance pricing
Some PETs just measure ad performance and don’t personalize. But when the same measurement system covers both harmful and win-win ad placements, it creates incentives for advertisers to chase the best possible metrics while creating the least possible value for the user. In a sustainable system, the user, or some party that the user trusts to provide an ad-supported resource, would be a data gatekeeper to keep data from leaking into the negative-sum corners of the Internet. People choose to provide their information to parties they trust—they don’t broadcast info about themselves to trusted and untrusted parties on the same terms.
how things got this farPETs started to go mainstream in the advertising scene back in 2019 when Google announced the Privacy Sandbox project. (Apple was first with wide release of a PET ad system, Private Click Measurement in 2021.) At the time, some people picked up on PETs as an alternative to platform dystopia, a way for independent retailers and publishers on the web to make a compromise and continue to do business without a hard dependency on fixing the Internet’s deeper monopolization, discrimination, and fraud problems. But in the about five years that people have been been arguing about web ad PETs, most recently over Google’s ongoing effort to make their PETs acceptable to the Competition and Markets Authority (CMA) in the UK, a big PET win is looking less and less likely. After all the work that has gone into PETs, not only do big risks remain, but—and this is super awkward—the companies working on PETs are still the same Big Tech companies that PETs were supposed to…protect us from?
Meanwhile, in the years since the PET trend began, mainstream privacy laws have gone off in a different direction, and focused not on obfuscation and math, but on data minimization and on enabling people to find out how companies use data. Data subject access rights, or “right to know,” are a key component of modern privacy laws and make it possible for web users and for organizations working on their behalf to detect patterns of illegal discrimination. In a 2019 settlement, Facebook agreed to stop using age, gender and ZIP code for housing, employment and credit ads. Reporters were later able to track the company’s progress. Privacy researchers and advocates continue to benefit from “right to know” processes today. A PET environment, however, limits access to data, making algorithmic discrimination hard to detect.
Much recent privacy news would have been as bad or worse in a PET environment. Grindr users aren’t suing over privacy because they were individually identified, they are suing because they were identified by HIV status, a fact common to a large group of people. Reviews of Google’s Privacy Sandbox, have, for quite a while, anticipated regulator concerns over algorithmic discrimination and transparency. The W3C TAG, in a review of a Privacy Sandbox” sub-project, wrote,
The Topics API as proposed puts the browser in a position of sharing information about the user, derived from their browsing history, with any site that can call the API. This is done in such a way that the user has no fine-grained control over what is revealed, and in what context, or to which parties. It also seems likely that a user would struggle to understand what is even happening; data is gathered and sent behind the scenes, quite opaquely.
Under privacy laws, users have the right to access not just their raw data, but the inferences made from it—a capability that will be difficult to retrofit into PETs. Google posted a FAQ stating,
Chrome can and will take steps to avoid topics that might be sensitive (i.e. race, sexual orientation, religion, etc.). However, it is still possible that websites calling the API may combine or correlate topics with other signals to infer sensitive information, outside of intended use. Chrome will continue to investigate methods for reducing this risk.
No results have been posted from this investigation so far. Someone will probably get a Best Paper award at a conference for solving algorithmic discrimination a PET-based ad system…eventually. Until that happens, PETs will struggle to meet basic transparency requirements in more and more jurisdictions. The data obfuscation problems introduced by PETs will also create compliance challenges in the area of competition policy. In a recent Google report (PDF) to the CMA, the company acknowledges that compliance with the Digital Services Act (DSA) by “Privacy Sandbox” publishers and advertisers remains an unsolved problem.
alternativesSo what do we do instead? PETs may continue to be valuable in fields like software telemetry, where the end result is all users receiving the same bug fixes, not different treatment of different users. But ads are a harder problem. First of all, PETs are not a shortcut to solving some important platform trust issues.
I see that your industry sold my parents a retirement scam, put malware in my search results, and showed fake repair shops on a map of my neighborhood…but I totally trust your answer to this complicated math problem. — no one everThe hard part about running any Internet service is the moderation (including ad review if it’s an ad-supported service). At some point Big Tech management needs to get over its dogmatic union-busting and sign fair contracts with the moderators and all the other people who do the high-skill human side of their operations. You can’t fix a reputation problem with math.
As far as how to make the ads work, it’s possible to get rid of third-party cookies and other problematic identifiers like mobile ad IDs without also taking on an open-ended research project. Instead of starting from what data flows are acceptable to today’s platforms/adtech/martech and trying to stick enough math on them to make them acceptable to users, start with how people choose to participate in markets and automate it. The Lindy Effect is a real thing in marketing. Ideas get tested out all the time, but the practices that tend to persist are the ones that have endured many generations of marketers, companies, and technologies. So the history of marketing practices that people have been willing to accept in the past is probably the best guide here. Realistically, markets will always have high and low reputation sellers, and the advertising most likely to persist will be whatever can pay for itself in (ad-supported resources + economic signal) > (cost in attention + resources + risk).
Finding something successful and sustainable and adapting it to the web is good for more total ad revenue over time—even if in any one transaction you get to capture less of it. A browser is a user agent, which means it does what users would do for themselves if they had time. People like to buy stuff, and prefer to buy better stuff. How can browsers help?
More: Sunday Internet optimism
Relatedturn off advertising features in Firefox
Google Chrome ad features checklist
turn off advertising measurement in Apple Safari
Bonus linksUsed. Today, though I make more money than ever before in my life, have more disposable income and am statistically in the top one-percent of American income-earners, there’s scarcely a brand or a product that tells me anything I feel I need to know about themselves.
Revenue-Share Orgy: Why Ad Agencies Are in Bed with Everyone We’re not going to fix our industry’s anemic ad-driven sales growth without rekindling the critical thinking, transparency, trust, and communication that originally built our business.
Glyph Lefkowitz: Against Innovation Tokens When programmers make a technology selection, we are often considering how difficult it will make the programming. Innovative technology selections are, by definition, less mature. That lack of maturity — particularly in the open source world — often means that the project is in a part of its lifecycle where it is concerned with development affordances more than operational ones. Therefore, the stereotypical innovative project, even one which might legitimately be a big improvement to development velocity, will create more operational overhead.
Fakespot reveals the product categories with the most and least reliable product reviews
Today, Fakespot, a free browser extension and website that protects consumers from unreliable reviews and sellers, announced the Amazon product categories with the most reliable and unreliable reviews, just in time for the big summer sales and back-to-school shopping season.
“We’re all about helping you shop smarter, especially during this month’s summer sales and the upcoming back-to-school season,” said Saoud Khalifah, co-founder and director of Fakespot. “Our latest report shows just how crucial it is to check those reviews, especially in categories flooded with unreliable reviews. By spotlighting both the best and worst categories, we give you the tools to shop with confidence.”
Since 2016, Fakespot has empowered millions of shoppers to make well-informed purchases using advanced AI technology. Its AI engine analyzes reviews, filters out unreliable ones and gives shoppers a true understanding of the quality of a product and the seller, so they can feel confident about their decisions. As a free browser extension available on most web browsers, Fakespot analyzes reviews from top e-commerce sites like Amazon, Best Buy, Sephora and Walmart, providing the most reliable product information before you buy. Bonus: The extension also provides seller ratings on Shopify-powered web stores.
When it comes to online shopping, knowing which products are trustworthy can save time and money. We are sharing our latest findings just in time for the shopping season. Our latest analysis has revealed some surprising and noteworthy stats (June 1, 2023 through May 31, 2024). Here are the most reliable and least reliable popular product categories:
Shop with confidence: Top 5 categories you can trustShop confidently with these top-rated products. These categories earned Fakespot Grades of B or better for reliability.
- Apple products: With an impressive 84% of reviews being genuine, Apple products stand out as a top choice for reliability. Only a tiny 5% of reviews are marked as unreliable.
- Video game chairs: Gamers, rejoice! 84% of reviews for video game chairs are trustworthy, making this a solid category for your next purchase.
- Books: Book lovers can breathe easy, as 81% of book reviews are authentic. Even with a whopping 2,907 products reviewed, books maintain a high standard of reliability.
- Computers: Tech enthusiasts, take note. Computers come in with 79% genuine reviews, ensuring you get the real scoop before buying.
- Home Office Desks: Perfect for remote work and homework, with 68% of reviews being legit.
Shop carefully and think twice before purchasing from these categories. These product categories have a Fakespot Review Grade of D or lower.
- Slides: A staggering 75% of reviews for slides are unreliable, making it the least reliable category in our study.
- Pajamas: Cozy up with caution, as 62% of pajama reviews aren’t genuine.
- Basketball: Sports gear shoppers should be wary, with 61% of basketball-related product reviews being unreliable.
- Stick vacuums and electric brooms: Housekeeping might need a bit more homework, with 57% unreliable reviews in this category.
- Fashion hoodies and sweatshirts: Fashion fans, beware. Over half (57%) of reviews in this category are not reliable, despite the large number of products reviewed (6,078).
Millions of Fakespot users depend on Fakespot’s Review Grade to help determine the reliability of the product reviews and seller. It follows the standard grading system of “A”, “B”, “C”, “D”, or “F” and represents the following:
- Fakespot Review Grade A and B: These grades represent reliable reviews.
- Fakespot Review Grade C: This grade should be approached with caution, as it includes a mix of reliable and unreliable reviews.
- Fakespot Review Grade D and F: These grades are considered unreliable.
We know just how crucial reliable reviews are in making informed purchasing decisions. Fakespot’s study sheds light on which categories are more prone to review manipulation, helping consumers make smarter, more informed choices.
So, whether it’s deal days or early back-to-school shopping, be sure to download Fakespot whenever you shop online.
 Shop confidently with Fakespot. Download the latest version today.
Shop confidently with Fakespot. Download the latest version today.
The post Fakespot reveals the product categories with the most and least reliable product reviews appeared first on The Mozilla Blog.
Mozilla Thunderbird: Welcome to Thunderbird 128 “Nebula”

On behalf of the entire team, the Thunderbird Council, and our global community of contributors, I’m excited to announce the initial release of Thunderbird 128 “Nebula.” This annual Extended Support Release (ESR) builds on the solid foundation established by Supernova last year.
Nebula ushers in significant improvements to Thunderbird’s code, stability, overall user experience, and the speed at which we can deliver new features to you.
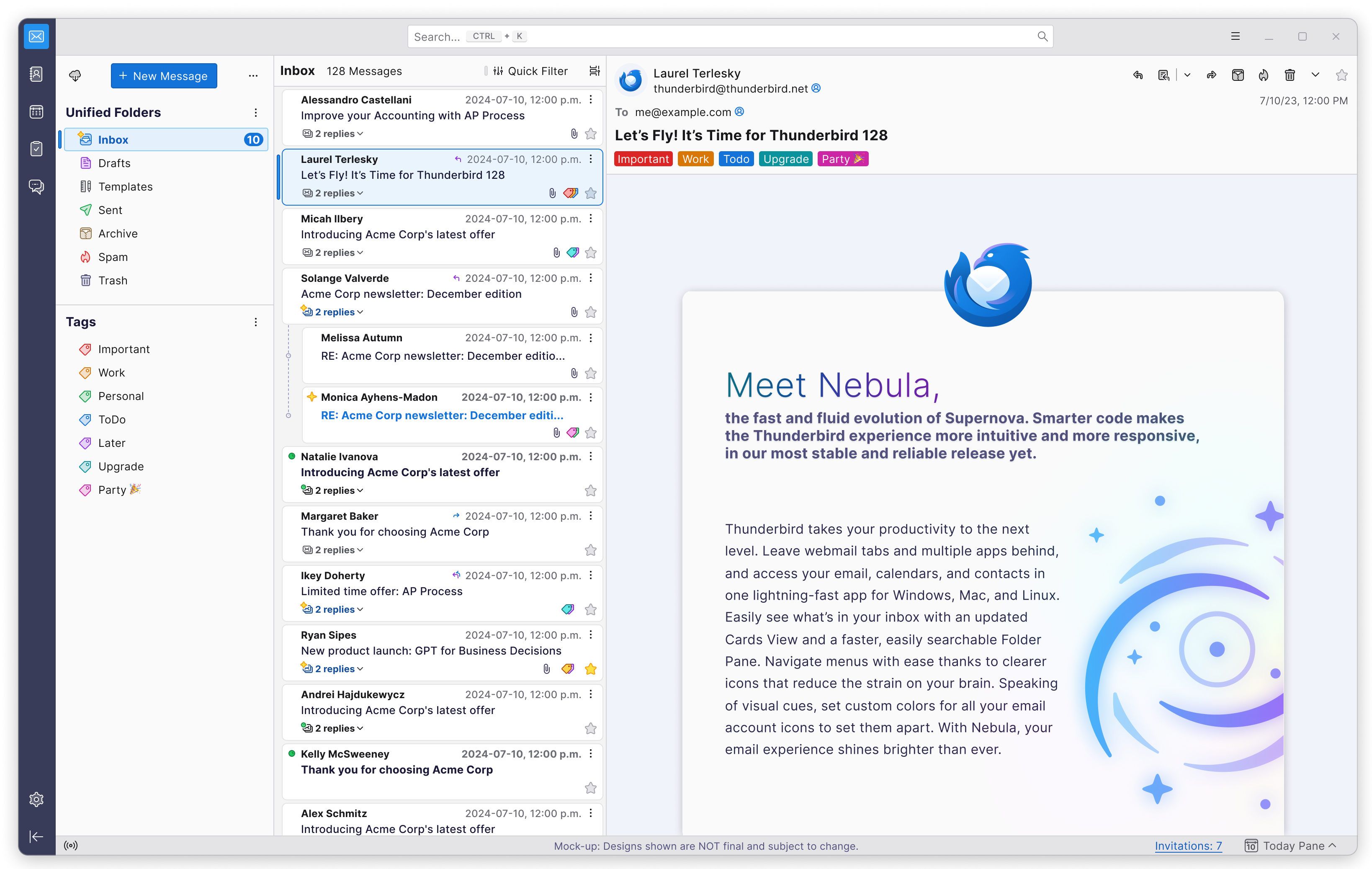
Here’s a small sample of what you can look forward to in this initial release.
Thunderbird 128: A Rust Revolution
We’ve devoted significant development time integrating Rust — a modern programming language originally created by Mozilla Research — into Thunderbird. Even though this is a seemingly invisible change, it is a major leap forward because it enhances our code quality and performance. This overhaul will allow us to share features between the desktop and future mobile versions of Thunderbird, and speed up our development process. It’s a win for our developers and a win for you.
Redesigned Cards View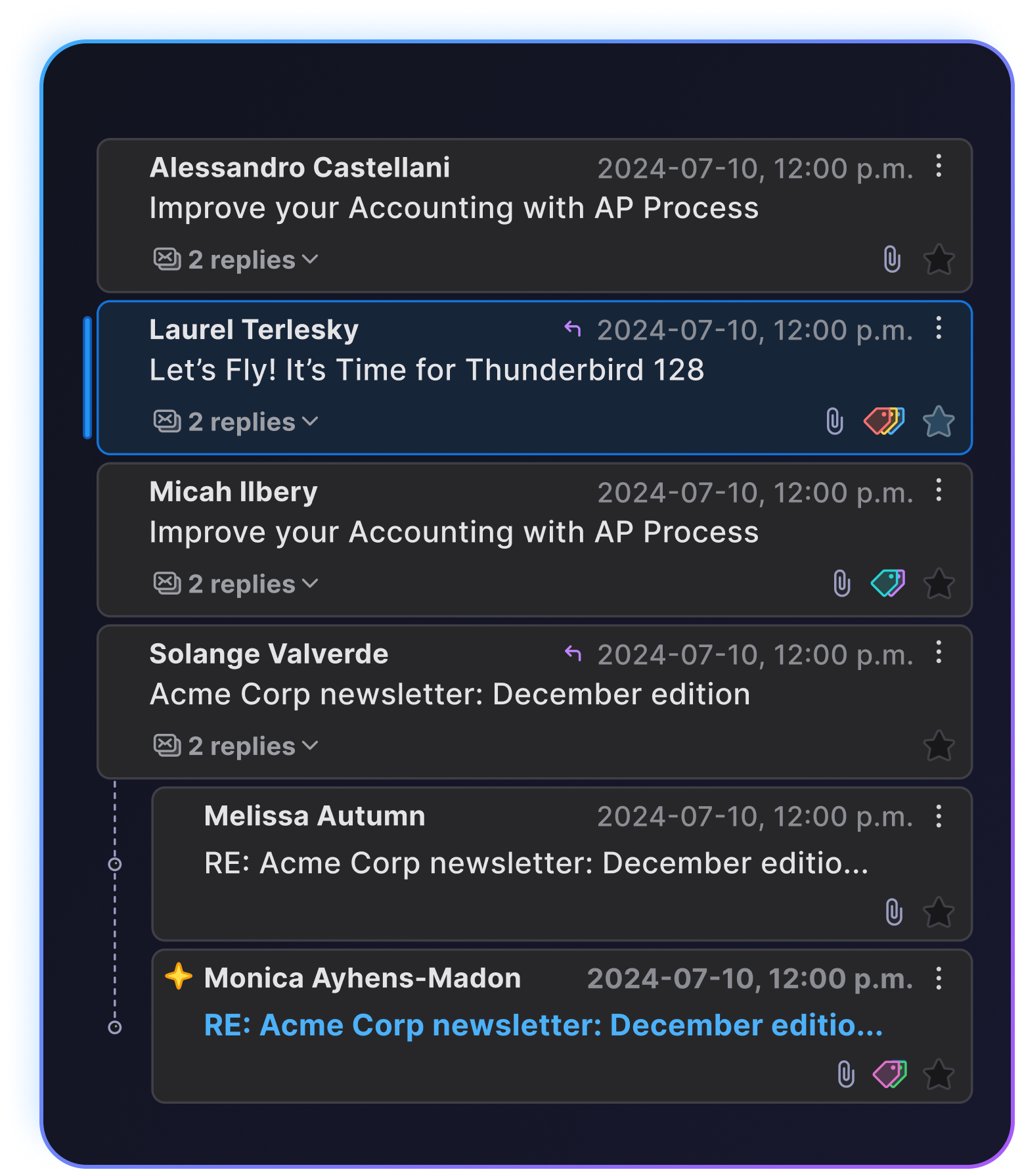
The Cards View, which debuted in 115 Supernova, has been tuned and refined for an even better experience. The new layout is more attractive and makes it easier to scan your email threads and glean information at a glance. Plus, the height of email cards adjusts automatically based on your settings, ensuring everything looks just right.
Enhanced Folder Pane
The Folder Pane has received several improvements, including faster rendering and searching of unified folders, better recall of message thread states, and multi-folder selection. We hope these changes make managing your folders faster and more intuitive.
 Accent Colors
Accent Colors
Thunderbird now offers improved theme compatibility, which is especially beneficial for our Linux users on Ubuntu and Mint. Your Thunderbird should blend seamlessly with your desktop environment, matching the system’s accent colors perfectly.
More Refinements & UpdatesAccount Color Customization: By popular demand, you can now customize the color of your account icons. These colors also appear in the “From” selection when composing emails, adding a light personal touch to your email experience.
Streamlined Menu Navigation: We’ve simplified menu navigation with better visual cues and reduced cognitive load. These enhancements make using Thunderbird more efficient and enjoyable.
Native Windows Notifications: Thunderbird’s native Windows notifications are now fully functional. Clicking a notification will dismiss it, bring Thunderbird to the foreground, and select the relevant message. Notifications also disappear when Thunderbird is closed, ensuring a seamless experience.
Improved Context Menu: The context menu has been reorganized for a smoother experience, with primary actions now displayed as icons for quick access.
Upcoming Exchange and Mozilla Sync FeaturesWe plan to launch the first phase of built-in support for Exchange, as well as Mozilla Sync, in a future Nebula point release (e.g. Thunderbird 128.X). Although these features are very close to being finished, technical obstacles prevented them from being ready today. Alex will keep you updated in his monthly Thunderbird Monthly Dev Digests.
For advanced users who want to help test our initial implementation of Exchange (currently limited to Mail), it is now available in our Daily and Beta builds. This Wiki page has more information as well as instructions for enabling it. While we definitely welcome your testing and feedback, please keep in mind this feature is currently experimental, and you may run into unexpected behavior or errors.
Looking Forward
In space, a supernova creates the building blocks of creation. In a nebula, those elements nurture new possibilities. Thunderbird 128 Nebula brings together and builds on the best of Supernova! Expect more updates and useful new features in the coming months.
Thank you for being a part of the growing Thunderbird community and sharing this adventure with us. Your feedback and support motivate us to chase constant improvements and deliver the best email experience possible.
[Updated July 31] Even with QA and beta testing, any major software release may have issues exposed after significant public testing. That’s why we are slowly enabling automatic updates until we’re confident no such issues exist. As of July 29, we have enabled manual upgrade to 128 via Help > About, and some users will begin receiving automatic updates. Thunderbird version 128.0 is also offered as direct download from thunderbird.net. For users running Thunderbird from the snap or flatpak, 128 is also available.
This post has been automatically translated from English to other languages by DeepL. Please forgive any grammatical or spelling errors.
The post Welcome to Thunderbird 128 “Nebula” appeared first on The Thunderbird Blog.
Mozilla heads to Capitol Hill, calls for a federal privacy law to ensure the responsible development of AI
 Udbhav Tiwari, Mozilla’s Director of Global Product Policy, testifies at a Senate committee hearing on the importance of federal privacy legislation in the development of AI.
Udbhav Tiwari, Mozilla’s Director of Global Product Policy, testifies at a Senate committee hearing on the importance of federal privacy legislation in the development of AI.
Today, U.S. Senator Maria Cantwell (D-Wash.), Chair of the Senate Committee on Commerce, Science and Transportation, convened a full committee hearing titled “The Need to Protect Americans’ Privacy and the AI Accelerant.” The hearing explored how AI has intensified the need for a federal comprehensive privacy law that protects individual privacy and sets clear guidelines for businesses as they develop and deploy AI systems.
Mozilla’s Director of Global Product Policy, Udbhav Tiwari, served as a key witness at the public hearing, highlighting privacy’s role as a critical component of AI policy.
“At Mozilla, we believe that comprehensive privacy legislation is foundational to any sound AI framework,” Tiwari said. “Without such legislation, we risk a ‘race to the bottom’ where companies compete by exploiting personal data rather than safeguarding it. Maintaining U.S. leadership in AI requires America to lead on privacy and user rights.” Tiwari added that data minimization should be at the core of these policies.
As a champion of the open internet, Mozilla has been committed to advancing trustworthy AI for half a decade. “We are dedicated to advancing privacy-preserving AI and advocating for policies that promote innovation while safeguarding individual rights,” Tiwari said.
The post Mozilla heads to Capitol Hill, calls for a federal privacy law to ensure the responsible development of AI appeared first on The Mozilla Blog.
Mozilla Thunderbird: Thunderbird for Android / K-9 Mail: June 2024 Progress Report

Is it July already? That means it’s time for another report on the progress of creating Thunderbird for Android.
Unfortunately, June has been one of these months without any flashy new features that would make for a nice screenshot to show off in a blog post. To not leave you hanging without any visuals, please enjoy this picture of Thunderbird team member Chris Aquino’s roommate Mister Betsy:

For a recap of the previous month’s activity, see May’s picture-less progress report.
New team memberThis year Thunderbird has hired a lot of new people. I’m very happy to report that this also included a manager who will coordinate all of our mobile efforts. Some of you may already know him. Philipp Kewisch has been working on the calendar integrated into Thunderbird for desktop and has been with the project in one capacity or another for a very long time. We’re very excited to have him (back).
Building two appsIn June we continued to work on making the necessary changes to be able to build two apps – K-9 Mail and Thunderbird for Android.
Volunteers working on translating the app have probably already noticed that we changed a lot of user-visible texts that included the app name. In cases where the app name wasn’t strictly necessary, we removed it. In other cases we added a placeholder, so the name of the app can be inserted dynamically.
We also worked on internal changes to make it easier to build multiple apps. However, there’s still quite a bit of work left. So don’t expect a fully working Thunderbird-branded version of the app to be available next week.
Material 3We’re still in the middle of migrating the user interface to Material 3. So far there hasn’t been any fine-tuning. What you currently see in beta versions of K-9 Mail is likely to change in the future. So we’re not looking for feedback on the design just yet.
Targeting Android 14In May the changes to target Android 14 were included in a beta release. After a few weeks of testing and not receiving any reports of problems, we included these changes in K-9 Mail 6.804, a maintenance release of the stable branch.
As a reminder, these changes are necessary so the app is not run in a compatibility mode on Android 14. It means the app supports the latest Android restrictions (e.g. when it comes to running in the background) and security features. Google Play enforces this by not allowing apps to publish updates without targeting Android 14 after the August 31 deadline.
More translationsThanks to the work of volunteer translators we were able to add support for the following languages to beta releases:
- Corsican
- Korean (was previously removed because coverage dropped below 70%)
- Vietnamese
In June 2024 we published the following stable release:
- K-9 Mail v6.804 (2024-06-07)
… and the following beta versions:
- K-9 Mail v6.902 (2024-06-21)
- K-9 Mail v6.903 (2024-06-24)
- K-9 Mail v6.904 (2024-06-27)
The post Thunderbird for Android / K-9 Mail: June 2024 Progress Report appeared first on The Thunderbird Blog.
Don Marti: turn off advertising features in Firefox
It’s understandable that Mozilla wants to break their dependency on Google search ads, but right now they seem to be doing it by, yes, yet again putting advertising features in the browser. This time they’re doing it in a way that introduces new, hard-to-understand risks. Google gets all the ink for their ad features in the browser project, but Firefox has given us some to-do items, too. I’ll keep this post up to date if the instructions change.
Privacy-preserving attributionPrivacy-preserving attribution (PPA) is the ad tracking thing cooperatively developed with Meta. It’s turned on by default as of Firefox 128, which is kind of a…bold…move, considering that even Google pops up a Got it dialog before turning on their ad stuff in Chrome. Here are the instructions for turning it off.
Click the menu button (≡) and select Settings.
In the Privacy & Security panel, find the Website Advertising Preferences section.
Uncheck the box labeled Allow websites to perform privacy-preserving ad measurement.
To turn off this feature in advance, before upgrading to Firefox 128, follow the instructions from Michael Kjörling:
Go to about:config
Create an entry:
dom.private-attribution.submission.enabled with a value of false.
That blog post also has info for disabling this by default in user.js which I have not tested.
Just putting privacy in the name of a feature doesn’t make it less creepy. Considering today’s branding trends it might even go the other way. Your privacy is important to us is the new your call is important to us. If you dig into the literature behind PPA, you will find some mathematical claims about how it prevents tracking of individuals. This is interesting math if you like that kind of thing. But in practice the real-world privacy risks are generally based on group discrimination, so it’s not really accurate to call a system privacy-preserving just because it limits individual tracking. Even if the math is neato.
(Meta has a big ongoing problem with AI-generated scam ads so even if you like personalized ads, this is still a good feature to turn off. Any tracking data passed to Meta will help them match scammers with victims, so you are doing other users a favor when you turn off your own tracking.)
Firefox for AndroidThom Holwerda posted:
- Go to chrome://geckoview/content/config.xhtml
- Use the search field to find the entry for aboutConfig and enable it
- Go to about:config
- Search for dom.private-attribution.submission.enabled and set it to false
(I have not tested this—if you have better instructions please let me know.)
Sponsored stuff on the new tab pageThese have been around for a while and do not seem to be a big deal, but just in case you’re creeped out by the whole PPA thing and on a roll with clicking around in settings…
Click the menu button (≡) and select Settings (if you’re not already in Settings from the previous tip)
In the Home panel, you have two options.
Change the New Windows and Tabs settings to Blank Page (fastest) or Custom URLs
Uncheck any or all of these boxes: Recommended by Pocket Sponsored shortcuts Sponsored Stories
These do seem harmless but if you’re in doubt because of the whole turn on Meta tracking without asking thing I can understand turning them off too.
Turn on Global Privacy ControlI’m going to end with some good news and ask, please don’t get mad at Firefox in general just because of one more fad-chasing move by management. I have been using this thing since it was Netscape Navigator, and even worked there for a while, and I have always been able to muddle through. Here is a place where Firefox is ahead of the other browsers.
This preference is a little tricker, since it’s under about:config.
Go to about:config (and accept any warning dialogs if you get them).
Search for globalprivacycontrol.
Change the setting to true.
You can check that it works by going to globalprivacycontrol.org. Look for GPC signal detected at the top of the screen.
Ad blocker checkMozilla seems to be doing better at keeping the scam ad blockers out of their extensions directory than Google—but that might just be that fewer malware developers are targeting Firefox now. But it is a good idea to check that your ad blocker is protecting you—privacy is now the number one reason why people install ad blockers. You can check your browser setup at EFF’s Cover Your Tracks site.
Work in progressThis is a work in progress, will update as needed. If you’re looking for info on the Mr Robot TV show plugin I think this is totally gone by now and you should not have to do anything.
Related“Privacy-Preserving” Attribution: Mozilla Disappoints Us Yet Again At the end of the day, Mozilla knows this feature isn’t something that Firefox users want. If they truly believed this was the one path away from the constant data theft perpetuated by the advertising industry, they would’ve announced this loudly and proudly.
remove AI from Google Search on Firefox While you’re on a roll removing crap that Big Tech wants you to like, might as well fix Google search results.
PET projects or real privacy? Some background info on privacy-enhancing ad personalization, which, to me, looks like an interesting technical dead end.
remove AI from Google Search on Firefox
Google Chrome ad features checklist covers how to turn off the ad stuff in Google Chrome.
turn off advertising measurement in Apple Safari (just one setting, but it’s buried under Advanced)
Red Hat Bugzilla Bug 2297635 - Firefox silently enables advertiser tracking and breaks privacy without user permission Firefox pushed an update that enabled prototype advertiser spying functionality and Fedora forgot to disable it by default
explainers/ppa-experiment at main · mozilla/explainers This is Mozilla’s POV about why they’re doing this. (They’re mixing up privacy protection and protection from individual addressability, which is a trend now, and an annoying one. As a privacy nerd, now I know how music nerds feel when people go on and on about Nickelback.)
Bonus linksThe Golden Calf Of Addressability: Reevaluating The Foundations Of Digital Advertising Advancements in AI have given us the tools to gather probabilistic insights by examining broader audience trends and modeling future behavior, rather than chasing the deterministic cookie trail to nowhere. (You still have to be careful—even if tracking is not deterministic it can still faciliate discrimination, matching scammers to victims, and other harms.)
The DOJ’s Witness List For The Google Antitrust Trial Is A Who’s Who Of Advertising (look, they released a list of all the people who know enough about web ads to give informed consent)
Support.Mozilla.Org: What’s up with SUMO – Q2 2024
Hi everybody,
As we wrap up the second quarter of 2024, it’s time to reflect on our accomplishments and the ongoing efforts within our community. It’s been a busy Q2. And many of you have made some of that work possible by really jumping in to help. It’s time to celebrate and look back on our accomplishments before we gather more strength again to continue our fights for the healthy internet.
Welcome note and shout-outs- Welcome to Basil Iqbal, Christian Lin, Sulaiman, Karan S, Dmitry K, and Isaac H. Thanks for joining the Social and Mobile Store Support program!
- Huge thanks to Marcelo, Luis A. Sánchez, Gerardo, Pierre, Artist, Cláudio, Wim, Tim, Mark H, Michele, Chris, Jim, Selim, Mahtab, Fauzan & Lidya, Haoran & Wxie, Irvin, Ronx & Bob, Hyeonseok, Daisuke, Quế Tùng, and Dmitry for helping out with localization work for the Firefox 3rd party installer campaign!
- Thanks to those who take care of the locale-specific forums in SUMO. Next for taking care of Italian, poljos and Ansam for taking care of cs, Gerardo for taking care of Spanish, Balázs Meskó for taking care of Hungarian, Selim for taking care of Turkish, and Wim for taking care of the newly opened NL forum. You’ve been wonderful, and your contribution is highly appreciated.
If you know anyone that we should feature here, please contact Kiki and we’ll make sure to add them in our next edition.
Community news- We shared the community strategy and the result of the contributor survey 2024 on the community call in May. Check it out if you haven’t got a chance to!
- Wiki page for Firefox release just got a new face since version 126. Check it out and let Kiki know if you have feedback on how to improve it!
- There’s a lot going on with content in SUMO. Make sure you’re updated with what we’re up to.
- There was an incident which caused X/Twitter to break on Firefox with Enhanced Tracking Protection set to strict mode (recap of the incident is in Firefox 126 wikipage), but we quickly react by posting a status update of the incident.
- Check out our new guideline on how to report inappropriate content in SUMO. This might be quite handy to share with new users!
- Check out the Firefox Reddit AMA if you haven’t!
- We released the Firefox 3rd party installer campaign on June 14, 2024! There’s still time to participate before we end the campaign on July 14!
- We released the first edition of the Contributor spotlight content last month featuring Wensheng Xie. Stay tuned for the next edition!
- We released a bunch of stuff with Kitsune 1.0.3 on May 15, 2024. There’s a recap of this release here, which includes group messaging capability, in-product indicator on a KB, and Google Analytics migration. You can also check out the full release note on GitHub.
- On May 30, 2024, we released an exciting change in Kitsune, which is KB metadata information. We also released an improvement to the article metadata with the release of Kitsune 1.0.6 on June 5, 2024. You may see this contributor thread to read the recap of this release.
- Join our discussions in the contributor forum to see what’s happening in the latest release on Desktop and mobile.
- Watch the monthly community call if you haven’t. Learn more about what’s new in April, May, and June! Reminder: Don’t hesitate to join the call in person if you can. We try our best to provide a safe space for everyone to contribute. You’re more than welcome to lurk in the call if you don’t feel comfortable turning on your video or speaking up. If you feel shy to ask questions during the meeting, feel free to add your questions on the contributor forum in advance, or put them in our Matrix channel, so we can answer them during the meeting.
- If you’re an NDA’ed contributor, you can watch the recording of our bi-weekly Release Meeting from AirMozilla to catch up with the latest product releases. You can also subscribe to the AirMozilla folder by clicking on the Subscribe button at the top right corner of the page to get notifications each time we add a new recording.
- Consider subscribing to Firefox Daily Digest to get daily updates (Mon-Fri) about Firefox from across the internet.
- Check out SUMO Engineering Board to see what the platform team is cooking in the engine room. Also, check out this page to see our latest release notes
I still haven’t got my hands on GA4 data, so stay tuned for KB and localization stats!
KBKB pageviews (*)
* KB pageviews number is a total of KB pageviews for /en-US/ only
Month Page views Vs previous month Apr 2024 May 2024 Jun 2024Top 5 KB contributors in the last 90 days:
KB LocalizationTop 10 locales based on total page views
Locale Apr 2024 (*) May 2024 (*) Jun 2024 (*) Localization progress (per July 8)(**) de 91% fr 86% zh-CN 100% es 24% ja 36% ru 100% pt-BR 41% It 100% pl 83% zh-TW 3% * Locale pageviews is an overall pageview from the given locale (KB and other pages) ** Localization progress is the percentage of localized article from all KB articles per localeTop 5 localization contributors in the last 90 days:
Forum SupportForum stats
Month Total questions Answer rate within 72 hrs Solved rate within 72 hrs Forum helpfulness Apr 2024 2,514 72.20% 11.14% 71.25% May 2024 2,529 63.31% 10.24% 64.57% Jun 2024 2,421 63.82% 10.24% 65.45%Top 5 forum contributors in the last 90 days:
Social Support Month Total replies Total moderation by contributors Reply conversion rate Apr 2024 22 54 40.74% May 2024 26 55 47.27% Jun 2024 28 78 35.90%Top 5 Social Support contributors in the past 3 months:
Play Store Support Month Total replies Total interactions Reply conversion rate Apr 2024 53 166 31.93% May 2024 141 271 52.03% Jun 2024 158 279 56.63%Top 5 Play Store contributors in the past 3 months:
Stay connectedMozilla Addons Blog: Manifest V3 updates landed in Firefox 128
With the release of Firefox 128 comes additional Manifest V3 improvements as the engineering team continues to make cross-browser compatibility work a key focus, especially related to content scripts and the scripting API.
In Firefox 128, support is now available for the MAIN execution world for content scripts declared in the manifest.json file and scripting.executeScript, which allows extensions to inject a script in the web page execution environment. However, unlike using window.eval from an isolated content script, the script injected into the MAIN world is not blocked by a strict webpage CSP. Please be aware that content scripts executed in the MAIN world do not have access to any WebExtension APIs.
Developers should also take note that the non-standard Web API events overflow and underflow have been deprecated. Use of these events should be removed from extension documents before the release of Firefox 131. Extension developers can set the “layout.overflow-underflow.content.enabled_in_addons” about:config preference to false in Firefox Nightly to determine whether their extensions will break in the future.
And to make migration less burdensome for developers, we intentionally back ported MV3 APIs to MV2. This means extensions developers will be able to more easily transition their extensions to MV3 gradually. For example, in Firefox 128, despite the fact that the MAIN world and the match_origin_as_fallback features are only supported for MV3 in Chrome, we will still support them on Firefox for MV2.
Lastly, with the launch of the Android permissions UI in Firefox 128, we are able to facilitate the control of the optional permissions and supporting host permissions that landed last month in Firefox 127. This means we are now able to fully support MV3 on Firefox for Android.
For a list of all changes relevant for add-on developers available in Firefox 128, please see our release notes. For more information on adopting MV3 in general, check out our migration guide. If you have questions or comments on our Manifest V3 updates we would love to hear from you in the comments section below or if you prefer, drop us an email.
The post Manifest V3 updates landed in Firefox 128 appeared first on Mozilla Add-ons Community Blog.
Support.Mozilla.Org: Cognitive Load Reduction Initiatives: Mid-Year Update
Hello, SUMO Community! As we kick off the second half of 2024, we’re thrilled to share the progress the CX Content Team has made this year in our Cognitive Load Reduction Initiatives. Our goal? To make SUMO articles more accessible, user-friendly, and visually appealing. Here’s a look at what we’ve accomplished so far and a sneak peek at what’s coming next.
Phase 1: Optimizing image use- Simplified user interface (SUI) screenshots: We have updated existing screenshots with simplified versions that focus on crucial visual elements. This reduces complexity and makes it easier for users to understand.
- Inline screenshots and icons: We have added inline screenshots and icons to enhance our articles by visually demonstrating interface elements, making instructions clearer, and improving user comprehension.
- Sequential step markers: We have opened the possibility of using numbered annotations on product screenshots to consolidate various actions into a single image. This reduces the number of screenshots needed and makes articles clearer and more concise.
- Integrating animated GIFs: We plan to incorporate GIFs into key articles where they can be most effective. These GIFs will visually illustrate processes that would otherwise require multiple static images, enhancing user comprehension and engagement.
- Merging and reorganizing content: We plan to redesign key articles to support multiple platforms, consolidating information into one comprehensive article. Platform-specific details will be organized using tabs or collapsible sections. We will also reorganize and merge similar articles to enhance clarity and ease of use.
We look forward to continuing this journey in the second half of 2024, making SUMO an even more valuable resource for our users. Thank you to all our contributors for your hard work and dedication to these initiatives. Together, we’re making a huge impact on the Firefox support experience.
Don Marti: Using GitHub Pages to host a locally built site
Something I recently ran into: How do you build a site locally and host the resulting built version of the site on GitHub Pages? Here’s one way to do it. First, have a make all target that builds the public files from the source pages (for example, pass CommonMark filenames to Pandoc to get HTML.) Then make deploy does several things:
- Make a fresh build directory and copy the source files, the Makefile, and the .git directory into it.
- Run make gh-pages inside the build directory. That target depends on the all target, so this builds the site inside the directory.
- Next, make gh-pages inside the build directory commits the public files on the gh-pages branch, then force pushes to GitHub.
- Back in make deploy, delete the build directory. That includes the .git directory inside, so no history of built files gets preserved.
This is from a Makefile for a very basic .org site. The -C option to make is to change to the given directory before reading the Makefile. (That site has versioning for the source files on GitHub too, but it doesn’t have to be.)
Another option is to put the built files in a subdirectory, but then you end up committing the built files on the main branch: Using different static site generators · community · Discussion #21563
Relatedplanning for SCALE 2025 is about some ideas for a conference talk on making a site using a Makefile and a bunch of various stuff instead of a static site generator.
Bonus linkshangout_services/thunk.js It turns out Google Chrome (via Chromium) includes a default extension which makes extra services available to code running on the *.google.com domains
Even Amtrak was surprised by the instant popularity of its new Chicago-Twin Cities route (how is this surprising? Who actually likes air travel or taking most of a day to drive between Midwestern USA cities?)
Microsoft-owned adtech Xandr accused of EU privacy breaches (among the fun parts about this story is that they’re not bottlenecked on Ireland—noyb.eu figured out a way to file the complaint in Italy)
A high-level view of all of this feed reader stuff (good info about a useful QA service for making your RSS tool better behaved. The script that builds the links for this bonus links section just got fixed up some.)
Design for the People: The US Web Design System and the Public Sans Typeface To ensure clear and consistent typography, the free and open-source typeface Public Sans was created for the US government.
Download the Atkinson Hyperlegible Font | Braille Institute Atkinson Hyperlegible font is named after Braille Institute founder, J. Robert Atkinson. What makes it different from traditional typography design is that it focuses on letterform distinction to increase character recognition, ultimately improving readability. (If I use a hyperlegible typeface, I can make my prose more confusing, right?)
The Itanic Saga (personally I had no idea that a story about Intel Itanium would start in 1923)
Amazon Is Investigating Perplexity Over Claims of Scraping Abuse Amazon’s cloud division has launched an investigation into Perplexity AI. At issue is whether the AI search startup is violating Amazon Web Services rules by scraping websites that attempted to prevent it from doing so, WIRED has learned.
Firefox Add-on Reviews: Fakespot — your friend in the fight against unreliable reviews
There may be differing opinions about the health benefits of vitamin supplements, but there’s no debate among medical experts that eating sawdust is bad for you. Yet sawdust is exactly what Saoud Khalifah found in vitamin supplements he ordered online from a globally popular shopping site. How could this have happened, he wondered? Khalifah started digging and discovered an overwhelming number of unreliable product reviews on many of the world’s biggest eCommerce sites.
That revelation back in 2016 inspired Khalifah to assemble a team and develop Fakespot — an extension that utilizes generative artificial intelligence (GenAI) to analyze the reliability of product reviews. Fakespot can analyze reviews on Amazon, Best Buy, Walmart, Sephora, eBay and Shopify-powered sites, with coverage for more shopping platforms in the pipeline. Sensing an opportunity for great collaboration, the Fakespot team joined Mozilla last year to further advance its mission to arm users with information about product reviews and pursue other GenAI projects.
Rob Gross, Fakespot Senior Manager, explains that part of what makes Fakespot so effective are the seven years experience their team has accrued deploying “state-of-the-art AI and constantly improving our platform to find emerging problematic patterns and stop them before they spread.”
 <figcaption class="wp-element-caption">Fakespot Review Grades indicate how reliable the reviews are, not the product.</figcaption>
<figcaption class="wp-element-caption">Fakespot Review Grades indicate how reliable the reviews are, not the product.</figcaption>
When unreliable product reviews started to emerge en masse online about a decade ago, they were the written work of actual people employed at “fake review farms” and still are today. But now the “fake review farms” and others have the power of GenAI to help them mass produce reviews, which compounds the complexity and scale of this phenomenon. However the root problem remains the same. “The issue with GenAI-derived reviews have the same issues as human-generated ones,” explains Gross. “They have patterns that Fakespot can detect and we are constantly working to update our engines to detect new and emerging forms of potential consumer deception.
Give yourself a fighting chance against a rising tide of unreliable reviews and try Fakespot. It’s intuitive, easy to use, and improves all the time.
Firefox Developer Experience: Firefox WebDriver Newsletter — 128
WebDriver is a remote control interface that enables introspection and control of user agents. As such it can help developers to verify that their websites are working and performing well with all major browsers. The protocol is standardized by the W3C and consists of two separate specifications: WebDriver classic (HTTP) and the new WebDriver BiDi (Bi-Directional).
This newsletter gives an overview of the work we’ve done as part of the Firefox 128 release cycle.
ContributionsFirefox – including our WebDriver implementation – is developed as an open source project, and everyone is welcome to contribute. There were no external contributions during the Firefox 128 release cycle, but I’m sure we will have more in the next cycles. If you ever wanted to contribute to an open source project used by millions of users, or are interested in some experience in software development, we have many beginner-friendly available over at https://codetribute.mozilla.org/.
General Support for the extended “unhandledPromptBehavior” capabilityWe now support the extended “unhandledPromptBehavior” capability which can either be a string (for WebDriver Classic) or a JSON object (for WebDriver BiDi). The JSON object can be used to configure a different behavior depending on the prompt type, which is useful for instance to handle “beforeunload” prompts.
{ "unhandledPromptBehavior": { "default": "accept and notify", "beforeUnload": "accept" } } WebDriver BiDi Support for the “BiDi flag”We now support the “BiDi flag” of a WebDriver Session to align with the WebDriver BiDi specification. This allows to identify sessions created for or upgraded to WebDriver BiDi.
Support for several arguments for the `network.continueRequest` commandIn previous releases, we introduced commands to intercept and resume requests, such as network.addIntercept and network.continueRequest. With Firefox 128 we now support most of the optional parameters for network.continueRequest, which means you can now modify requests blocked in the beforeRequestSent phase. The available parameters are body, cookies, headers and method. The modification will happen before the request is sent to the server, so this can be used for instance to add some test-specific headers to certain requests.
-> { "method": "network.continueRequest", "params": { "request": "12", "headers": [ { "name": "test-header", "value": { "type": "string", "value": "42" } } ] }, "id": 2 } <- { "type": "success", "id": 2, "result": {} }Take a look at the specification to learn more about the types for the new parameters. There is still one parameter to implement for network.continueRequest which is url and will allow to redirect a request to another URL, hopefully coming soon.
Also note that before Firefox 128, the requests blocked in the beforeRequestSent phase could still intermittently be blocked a bit late and reach the server. This should now be fixed, and requests blocked in this phase should not reach the network until resumed.
Support for the `userContext` argument in the `permissions.setPermission` commandWe now support the userContext argument for permissions.setPermission, which allows to isolate a specific permission update to a single user context (Firefox Container). userContext is expected to be a string corresponding to the id of a user context.
Bug fixes- Fixed a bug in `browsingContext.navigate` where a navigation error would load an error page and cause subsequent commands to fail.
- Fixed the order in which `network.responseCompleted` events are emitted for redirects. The original request’s responseCompleted is now always emitted before the events for the redirect.
- Introduced a workaround to not partition cookies which are added with the “storage.setCookie” command for the same domain as the page loaded in the targeted context. This aligns with the current behavior of Firefox, and will be updated as support for CHIPS in Firefox progresses.
- The input.setFiles command has been updated to throw an UnsupportedOperation error if the specified file does not exist.
Similar to the “BiDi flag”, we also added support for the “HTTP flag” of a WebDriver Session. This allows to identify sessions created for WebDriver classic.
Support for the Permissions API in WebDriver ClassicFollowing the work in WebDriver BiDi in previous releases, we added support for the Permissions commands in WebDriver Classic.
